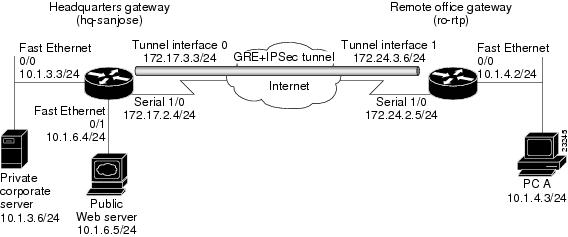
Basic EIGRP configuration lab
1. Prepare network
2. Perform Basic Router configuration
3. Configure and activate serial and ethernet address
4. Configure EIGRP on the R1 router
5. Configure EIGRP on the R2 and R3 router
6. Verify EIGRP operation
7. Examine EIGRP Routes in the Routing tables
8. Configure EIGRP metrics
9. Examine Successors and Feasible Distances
10. Determine if R1 is a Feasible Sucessor for the Route from R2 to the 192.168.1.0 network
11. Examine the EIGRP topology table
12. Disable EIGRP Automatic Summarization
13. Configure Manual summarization
Challenge EIGRP configuration lab
1. Subnet the address space
2. Determine Interface address
3. Prepare the network
4. Perform basic router configurations
5. Configure and activate serial and ethernet address
6. Verify connectivity to Next-hop device
7. Configure EIGRP routing on the Branch1 Router
8. Configure EIGRP and static routing on the HQ router
9. Configure EIGRP routing on the BRANCH2 Router
10. Verify the configurations
11. Reflection
EIGRP troubleshooting lab
1. Prepare network
2. Perform Basic Router configuration
3. Configure and activate serial and ethernet address
4. Configure EIGRP on the R1 router
5. Configure EIGRP on the R2 and R3 router
6. Verify EIGRP operation
7. Examine EIGRP Routes in the Routing tables
8. Configure EIGRP metrics
9. Examine Successors and Feasible Distances
10. Determine if R1 is a Feasible Sucessor for the Route from R2 to the 192.168.1.0 network
11. Examine the EIGRP topology table
12. Disable EIGRP Automatic Summarization
13. Configure Manual summarization
Challenge EIGRP configuration lab
1. Subnet the address space
2. Determine Interface address
3. Prepare the network
4. Perform basic router configurations
5. Configure and activate serial and ethernet address
6. Verify connectivity to Next-hop device
7. Configure EIGRP routing on the Branch1 Router
8. Configure EIGRP and static routing on the HQ router
9. Configure EIGRP routing on the BRANCH2 Router
10. Verify the configurations
11. Reflection
EIGRP troubleshooting lab